SOC Automation Explained: What It Is and Why It Matters in 2025

Cybersecurity in 2025 looks very different from just a few years ago. Threat actors are faster, more automated, and more relentless than ever, and traditional SOCs can’t keep up with the scale of alerts and attacks. That’s where SOC automation steps in.
In this guide, we’ll break down:
- What SOC automation really means
- The benefits of SOC automation for organizations in 2025
- Technologies & Tools Driving SOC Automation
- How orchestration and automation work together in a SOC
- Metrics & KPIs for SOC Automation
- Challenges, Risks & Limitations of SOC Automation
- Why COGNNA’s Agentic AI approach takes automation further
By the end, you’ll understand not only how SOC automation reduces alert fatigue and speeds up response, but also why it’s quickly becoming the new standard for resilient cybersecurity operations.
What is SOC Automation?
Security Operations Centers (SOCs) are the nerve centers of modern cybersecurity; monitoring, analyzing, and responding to threats around the clock. But traditional SOCs face a challenge: endless alerts, manual processes, and human fatigue that slow down response.
SOC automation solves this by using advanced orchestration, artificial intelligence, and predefined playbooks to handle repetitive tasks. Instead of analysts chasing false positives, automation solutions for SOCs handle triage, escalation, and even response in real time.
In short: SOC automation empowers human analysts to focus on what matters most; critical threats and strategic defense.
Why SOC Automation Matters in 2025
2025 is a tipping point for cybersecurity. Attackers are scaling faster with AI-driven techniques, and organizations can’t keep up with manual monitoring. SOC automation isn’t just a “nice-to-have” anymore; it’s the foundation for resilience.
The benefits include:
- Faster Detection & Response – Reduce time to detect and contain incidents.
- Reduced Alert Fatigue – Automation filters noise, so analysts focus on real threats.
- Consistent Orchestration – Predefined playbooks ensure standardized, error-free responses.
- Better Visibility – Automated correlation across systems gives a unified view of risks.
- Lower Costs – Fewer manual hours wasted means smarter resource allocation.
Technologies & Tools Driving SOC Automation
The backbone of SOC orchestration and automation lies in advanced tools. Here’s what powers automation today:
- SIEM (Security Information and Event Management) – Collects and correlates logs, providing the foundation for automated analysis.
- XDR (Extended Detection and Response) – Expands visibility across endpoints, networks, and cloud.
- SOAR Platforms (Security Orchestration, Automation, and Response) – Automates workflows, integrates across systems, and executes playbooks.
- EDR (Endpoint Detection and Response) – Provides real-time endpoint monitoring and remediation.
- No-Code / Low-Code Workflows – Enable security teams to create automation rules without deep coding expertise.
- Cloud-Native Automation Tools – Essential for hybrid and multi-cloud environments.
While each of these tools has a critical role, many organizations struggle to weave them into a cohesive, efficient ecosystem. The result is often tool sprawl, integration headaches, and inconsistent workflows. This is where COGNNA stands apart.
By unifying SIEM, XDR, EDR, threat intelligence feeds, and our Agentic AI into one platform, COGNNA delivers a complete automation solution without the complexity of managing multiple vendors. Instead of stitching together point products, you get a seamless, end-to-end system that simplifies integration, reduces operational overhead, and powers truly intelligent SOC automation.
SOC Orchestration and Automation in Action
While automation is often seen as alert triage, its value extends across multiple threat scenarios. Mature SOCs in 2025 rely on automation across end-to-end incident lifecycles, not just single tasks.
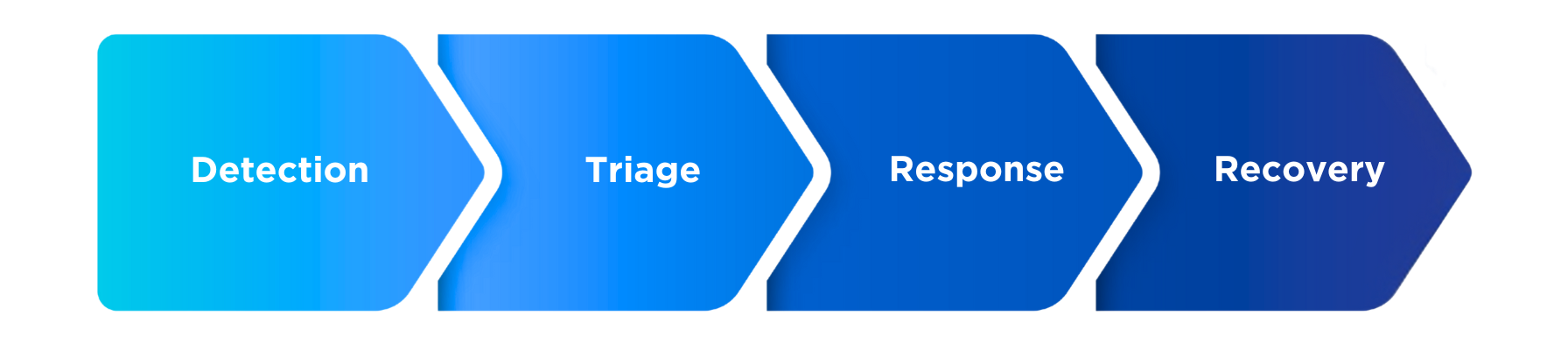
Here’s how it works in practice:
- Detection: Alerts are ingested from SIEM, XDR, and threat intelligence feeds.
- Triage: Low-priority alerts are automatically closed; suspicious ones are escalated.
- Response: Automated playbooks isolate endpoints, disable accounts, or block malicious IPs.
- Recovery: Workflows restore affected systems, while analysts review post-incident reports.
Below are expanded examples:
Metrics & KPIs for SOC Automation
How do you know if automation is delivering impact? Track measurable outcomes such as:
- Mean Time to Detect (MTTD) – Lower is better; automation can reduce from hours to minutes.
- Mean Time to Respond (MTTR) – Mature SOCs cut this by 60–80% with automation.
- False Positive Rate Reduction – Demonstrates efficiency gains for analysts.
- Percentage of Automated Workflows – A maturity indicator of how much the SOC relies on automation.
- Analyst Efficiency Gains – Measured by alerts handled per analyst per shift.
- Compliance Audit Readiness – Time saved in preparing regulatory evidence.
Challenges, Risks & Limitations of SOC Automation and How COGNNA Addresses Them
While SOC automation is transformative, it brings its own challenges. Here’s how COGNNA’s Agentic AI and platform directly address them.
How COGNNA Uses Agentic AI for SOC Automation

At COGNNA, we go beyond traditional orchestration. Our platform is built on Agentic AI, a system of intelligent agents that adapt dynamically to threats instead of just following rigid, predefined playbooks. This evolution means SOC automation is no longer reactive, but proactive, context-aware, and continuously learning.
- Context-Aware Decisions
Unlike traditional systems that evaluate alerts in isolation, COGNNA’s Agentic AI analyzes events in their full context. It understands relationships between logs, user behavior, and threat intelligence feeds, allowing it to distinguish real threats from noise and dramatically reduce false positives.
Example: Instead of flagging every suspicious login attempt, Agentic AI considers whether the login aligns with known user behavior, device reputation, and geographic anomalies before escalating it.
- Adaptive Playbooks
Static playbooks often fail in the face of evolving threats. COGNNA’s automation adapts in real time, modifying its response steps based on intelligence, feedback loops, and historical outcomes. This ensures that your SOC is always aligned with the threat landscape as it changes.
Example: In a phishing attack, the AI can block the malicious domain, revoke the compromised user’s session, and if it detects lateral movement, escalate containment automatically, without waiting for human input.
- Continuous Compliance
Every action taken by Agentic AI is mapped to regulatory frameworks such as SAMA and NCA, ensuring that automation strengthens compliance rather than creating gaps. This gives organizations confidence that security and compliance advance in lockstep.
Example: Automated evidence collection for incident reports ensures that organizations meet mandatory reporting timelines without manual delays.
- Guardians + AI: Augmented Human Expertise
At the heart of COGNNA’s philosophy is the belief that AI should augment, not replace. Human analysts—the Guardians—remain central to the decision-making process. Agentic AI handles the repetitive, high-volume tasks, freeing analysts to focus on strategic oversight and complex cases.
Example: Analysts no longer waste hours triaging false positives. Instead, they validate high-priority escalations with all contextual data already correlated by Agentic AI.
- Predictive Threat Anticipation
Agentic AI doesn’t just respond, it anticipates. By leveraging behavioral analytics, historical attack patterns, and global threat intelligence feeds, it can forecast potential attack vectors and prepare defenses before adversaries strike.
Example: Detecting abnormal privilege escalation trends before they lead to full account compromise.
- Seamless Ecosystem Integration
Agentic AI is built to unify the SOC ecosystem, integrating with SIEM, EDR, cloud monitoring, and identity platforms, to create a single, orchestrated layer of intelligence. This eliminates silos and ensures decisions are made with a holistic view of the environment.
Example: An endpoint malware alert in EDR is instantly correlated with identity data from IAM and cloud activity logs, ensuring the response is comprehensive and not fragmented.
This means faster response, fewer false positives, and stronger resilience against tomorrow’s threats.
The Road Ahead: SOC Automation as Standard
SOC automation isn’t just for large enterprises anymore. In 2025, it’s the baseline for organizations of all sizes. Whether you’re a fintech startup or a global enterprise, automated detection and response can mean the difference between minor disruption and catastrophic breach.
With COGNNA’s SOC automation solutions, you don’t just react, you stay ahead.
.webp)
.webp)



